Company Continuity Assurance: Your Trusted Partner in Corporate Security
Wiki Article
Professional Business Security Solutions to Ensure Service Connection
These solutions incorporate a detailed selection of actions, including physical security, cybersecurity solutions, risk assessment and monitoring, security training, emergency reaction, and case management. With a professional strategy and know-how in the area, corporate protection services offer companies with the peace of mind and confidence required to browse the complex safety landscape and keep organization connection.Physical Security Steps
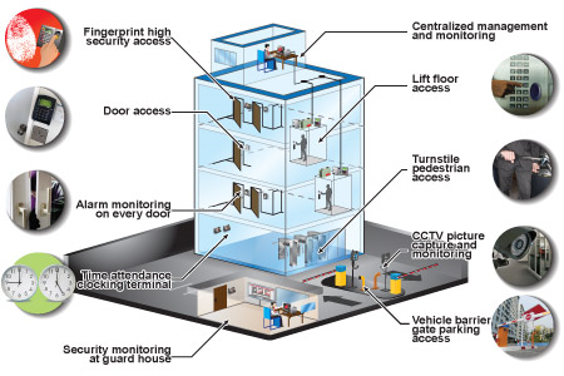
To make certain service connection, professional corporate safety solutions carry out rigid physical security steps. These steps are designed to secure the physical assets and facilities of an organization from unapproved access, burglary, criminal damage, and other prospective threats. Physical protection is a crucial part of total safety approach, as it supplies the first line of protection versus external threats.Among the key physical protection actions utilized by specialist corporate safety services is access control. This includes the installment of physical barriers such as gateways, turnstiles, and fences to control and manage access to the premises. Gain access to control systems may likewise consist of digital keycards, biometric scanners, and video surveillance to additionally enhance security.
Along with accessibility control, expert company safety and security solutions likewise concentrate on securing the physical atmosphere through making use of safety and security guards and patrols. Educated protection workers are stationed at essential factors throughout the facilities to keep an eye on and respond to any type of dubious task. Routine patrols are performed to ensure that all locations are adequately kept an eye on and to hinder possible burglars.
Furthermore, physical security actions additionally consist of the setup of safety systems such as alarms, activity sensing units, and CCTV cams. These systems give day-and-night surveillance and allow fast discovery and action to any security violations.
Cybersecurity Solutions
Expert company safety services use robust cybersecurity remedies to secure the digital framework and sensitive information of organizations, reducing the threats of cyber risks and guaranteeing business connection. In today's interconnected globe, where companies heavily count on digital systems and networks, cybersecurity has actually become a vital aspect of business security.Cybersecurity remedies incorporate a wide variety of measures created to protect versus unauthorized access, information violations, and other cyber dangers. These options consist of firewall programs, invasion discovery and avoidance systems, anti-viruses software application, security, and multi-factor authentication. By executing these measures, companies can reduce the susceptability of their digital properties and make certain the privacy, honesty, and accessibility of their data and systems.
One trick aspect of cybersecurity options is aggressive risk surveillance and event feedback. This involves constantly keeping an eye on networks and systems for any questionable tasks or abnormalities and responding immediately to any type of spotted dangers. Via real-time tracking, companies can recognize and address potential safety and security breaches before they cause significant damage.
In addition, employee training and recognition are important parts of cybersecurity solutions. Organizations need to enlighten their employees concerning best methods for cybersecurity, such as developing solid passwords, avoiding phishing scams, and being attentive concerning dubious e-mails or web sites. By cultivating a culture of safety and security understanding, organizations can substantially minimize the chance of human mistake causing cyber occurrences.
Danger Analysis and Monitoring
A thorough risk evaluation and monitoring procedure is crucial for efficiently recognizing and minimizing prospective threats to a company's safety and security and guaranteeing company connection. Danger analysis involves the organized identification and analysis of prospective risks that can impact an organization's procedures, properties, and credibility. It assists organizations understand the probability and possible effect of risks, enabling them to prioritize and allot sources to address the most crucial hazards.The initial step in the risk evaluation procedure is to identify and classify potential risks, such as physical protection breaches, cyber dangers, natural catastrophes, or inner fraud. When the risks are determined, they are assessed based on their likelihood of event and potential effect on the organization. This analysis helps figure out the level of danger connected with each danger and allows the growth of appropriate mitigation techniques.
Danger administration entails the execution of measures to get rid of or minimize recognized threats. This can consist of executing protection controls, such as accessibility control systems, surveillance cameras, fire alarms, and invasion discovery systems. Regular monitoring and evaluation of these controls guarantee their performance and allow prompt adjustments as required.
Safety And Security Training and Awareness Programs
Reliable security training i loved this and understanding programs are important for furnishing workers with the expertise and abilities necessary to safeguard firm possessions and reply to possible dangers. In today's quickly progressing organization landscape, companies encounter a raising variety of safety dangers, including cyberattacks, data breaches, and physical dangers. Consequently, it is critical for firms to buy detailed training programs that educate staff members regarding these dangers and exactly how to minimize them.Safety training programs ought to cover a variety of topics, consisting of best techniques for data defense, determining and reporting suspicious tasks, and reacting to emergencies. By giving workers with the necessary tools and knowledge, organizations can encourage them to take an active duty in protecting company assets. corporate security. This not just assists secure sensitive details yet additionally improves the general security pose of the company
In addition, awareness programs play a crucial role in making sure that employees stay vigilant and stay upgraded on the current protection risks and fads. These programs can include routine protection bulletins, e-newsletters, and training sessions that highlight emerging risks and supply practical ideas for maintaining a safe and secure work atmosphere. By maintaining employees notified and involved, organizations can cultivate a society of protection understanding and encourage positive actions.
Emergency Reaction and Case Management
- An integral aspect of business protection solutions is the implementation of a detailed emergency situation feedback and incident management plan. This plan is vital for ensuring the safety and wellness of staff members, customers, and possessions in case of any kind of emergency or event.
The initial step in creating a reliable emergency situation action and event management strategy is to perform a comprehensive risk analysis. This analysis assists identify potential threats, susceptabilities, and crucial areas that require to be resolved in the strategy. corporate security. When the risks are identified, appropriate measures can be taken to alleviate them
The emergency situation response strategy ought to include clear standards and methods for different kinds of emergency situations, such as all-natural catastrophes, fires, medical emergency situations, or protection breaches. It should lay out the functions and responsibilities of vital employees, communication protocols, discharge procedures, and the establishment of a command facility.
Incident administration concentrates on the prompt feedback to an event and the subsequent recovery and reconstruction of regular operations. It includes evaluating the seriousness of the incident, activating the action strategy, collaborating resources, and guaranteeing efficient communication between all stakeholders. The occurrence monitoring plan may also consist of treatments for recording and examining occurrences to avoid future events.

Final Thought
In verdict, expert corporate safety services sites play an essential duty in guaranteeing business connection. By carrying out physical safety and security steps, cybersecurity solutions, risk assessment and administration techniques, security training and recognition programs, in addition to emergency action and event monitoring methods, companies can mitigate possible dangers and guard their operations. These detailed safety actions are necessary for keeping a safe and resilient organization atmosphere.These solutions include a thorough variety of steps, consisting of physical safety, cybersecurity options, danger evaluation and administration, safety and security training, emergency situation action, and event administration. With a professional approach and know-how in the field, company protection solutions supply companies with the peace of mind and self-confidence required to navigate the complex security landscape and keep service continuity.
By carrying out physical safety and security steps, cybersecurity solutions, danger assessment and monitoring strategies, security training and awareness programs, as well as emergency action and case management protocols, services can reduce possible risks and guard their operations. (corporate security)
Report this wiki page